Non-Functional Testing : Introduction
- Non-functional testing is the type of testing which can be used to assess the non-functional requirements of the software product rather than the functional requirements.
- The non-functional requirement can include the performance of the software product, its scalability, or its usability.
Non-Functional Testing : Need
- It provides a great influence on customers regarding their satisfaction with the product.
-
Non-Functional testing deals with:
- The time taken by the software product to complete a particular task.
- The response time of the software product.
- Compatibility of the software product.
- Compliance of the software product.
- Opertebility of the software product.
Non-Functional Testing : Techniques
- There are four major non-functional testing techniques. These are:
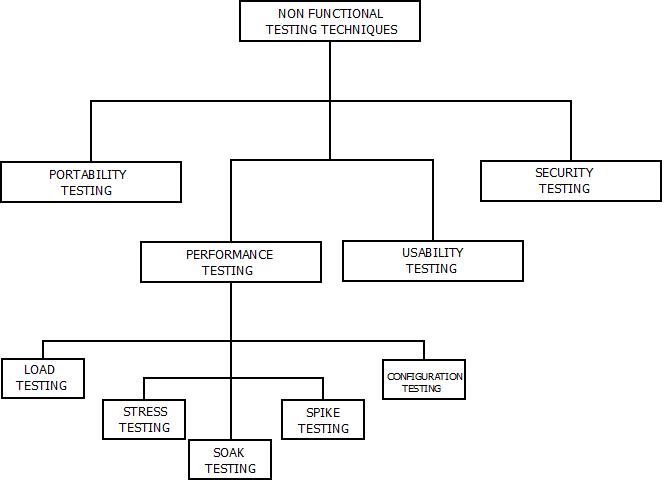
Non-Functional Testing : Techniques
-
Portability Testing
- Portability testing means to test the ability of the software product and its components for its effectiveness on one platform to other irrespective of the environment.
-
Performance Testing
- Performance testing means the process of evaluating the quality of the software product under certain conditions for its various abilities.
- Stress, Load, Soak, Spike and Configuration testing are the examples of performance testing technique.
-
Usability Testing
- Usability testing means to test the ability of a software product, whether it fulfils the requirements, expectations and specifications of users.
- It also deals with the amount of satisfaction attained by the users.
-
Security Testing
- Security testing is done to check a software product for security flaws.
-
Security testing includes the following factors:
- Integrity.
- Confidentiality.
- Authenticity.
- Authorization.
- Availability.
- It is process that enables to reveal loopholes and snags in the information systems in order to provide security to the user data.